Attack Trees
Attack trees are a
convenient way to explore potential attacks and thoroughly examine the
"attack space". An attack tree is simply a tree that is similar to a
logical decision tree used to perform a systematic analysis of the attack space
in terms of what is under attack, where the attack could happen, when the
attack could take place and how the attack could happen.
To illustrate the key
points, let us develop an attack tree against a physical safe (see Figure 1).
The goal of attackers is to open the safe. To open the safe, attackers have
several options: they can pick the lock, learn the combination, cut open the
safe, or install the safe improperly so that they can easily open it later. Now
you can assign values -- I (impossible) and P (possible) in this figure -- to
the leaf nodes to indicate what needs to be considered next. You can now pursue
the nodes that are possible for further evaluation. Let us now evaluate
"learn the combination" node and break it into two activities: find
the combination written down or get the combination from the safe owner through
eavesdropping or other means. Each node becomes a subgoal,
and children of that node are ways to achieve that subgoal.
In the attack trees,
there are
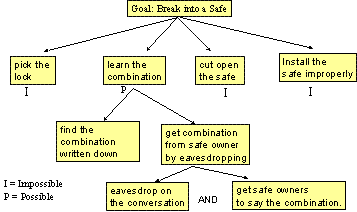
Figure 1: Sample Attack
Tree for Opening a Physical Safe (Shneier 1999)
See the paper on attack
trees by Bob Schneier (www.schneier.com/paper-attacktrees-ddj-ft.html)
for additional details.