| ACL |
Authorized Control List |
| ACM |
Association of Computing Machinery |
| AI |
Artificial Intelligence |
| AIA |
Application Integration Architecture |
| API |
Application Programming Interface |
| ASP |
Application Service Provider |
| ASP |
Active Server Pages A Microsoft technology for building
server side code |
| ATM |
Asynchronous Transfer Mode a packet switching Technology
used typically in high data rate networks |
| ATM |
Automatic Teller Machine used in banking |
| B2B |
Business to Business |
| B2C |
Business to Consumer |
| B2E |
Business to Employee |
| B2G |
Business to Government |
| BREW |
Binary Runtime Environment for Wireless |
| BSP |
Business System Planning |
| CAD |
Computer Aided Design |
| CAM |
Computer Aided Manufacture |
| CBX |
Computerized Branch Exchange |
| CCITT |
Comit Consultatif Internationale de Tlgraphique et Tlphonique
(The International Telegraph and Telephone Consultative Committee) |
| CDMA |
Code Division Multiple Access |
| CDPD |
Cellular Digital Packet Data |
| CGI |
Common Gateway Interface - A Web gateway technology |
| CIO |
Chief Information Officer |
| CORBA |
Common Object Request Broker Architecture |
| COTS |
Commercial Off-The-Shelf |
| CPU |
Central Processing Unit |
| CRM |
Customer Relationship Management |
| CSF |
Critical Success Factors |
| CSMA/CD |
Carrier Sense Multiple Access/Collision Detect |
| DBMS |
Database Management System |
| DCOM |
Distributed Component Object Model |
| DDBMS |
Distributed Database Management System |
| DDL |
Data Definition Language used in database management
|
| DDTMS |
Distributed Data and Transaction Management System |
| DML |
Data Manipulation Language |
| DOD |
Department of Defense |
| DSL |
Digital Subscriber Loop |
| DTM |
Distributed Transaction Manager |
| DTMS |
Distributed Transaction Management System |
| EAI |
Enterprise Application Integration |
| EB |
Electronic Business |
| EC |
Electronic Commerce |
| EDI |
Electronic Data Interchange |
| EJB |
Enterprise Java Beans |
| ERP |
Enterprise Resource Planning |
| ETSI |
European Telecommunication Standards Institute |
| FCC |
Federal Communications Commission |
| FDDI |
Fiber Distributed Data Interface |
| FDM |
Frequency Division Multiplexing |
| FSO |
Free Space Optics |
| FTP |
File Transfer Protocol |
| GUI |
Graphical User Interface |
| I/O |
Input/Output |
| IDL |
Interface Definition Language used in CORBA and other distributed
object middleware services |
| IEEE |
Institute for Electrical and Electronic Engineers |
| IMS |
Information Management System - IBM DB/DC system on mainframes |
| IP |
Internet Protocol |
| IPC |
Interprocess Communication |
| IRM |
Information Resource Management a management methodology |
| ISDN |
Integrated Services Digital Network |
| ISO |
International Organization for Standardization |
| ISP |
Internet Service Provider |
| IT |
Information Technology |
| ITU |
International Telecommunications Union |
| ITU-T |
International Telecommunications Union - Telecommunications
Services Sector |
| J2EE |
Java Version 2 Enterprise Edition |
| J2ME |
Java Version 2 Mobile Edition |
| JDBC |
Java Database Connectivity |
| LAN |
Local Area Network |
| LDBMS |
Local Database Management System |
| LLC |
Logical Link Control |
| LMDS |
Local Multipoint Distribution Service |
| LU |
Logical Unit - an endpoint in the IBM SNA environment |
| MAC |
Medium Access Control |
| MAN |
Metropolitan Area Network |
| Mbps |
Million bits per second |
| MMIT |
Microsoft Mobile Internet Toolkit |
| MOM |
Message Oriented Middleware |
| MVS |
Multiple Virtual System - operating system on IBM's mainframes |
| NBS |
National Bureau of Standards |
| NFS |
Network File Services - SUN Microsystem's File System for
Networks |
| NIST |
National Institute of Standards and Technology |
| OAG |
Open Application Group a standards organization |
| ODBC |
Open Database Connectivity a de-facto standard for remote
SQL |
| OMA |
Open Mobility Alliance |
| OMG |
Object Management Group the group that developed CORBA
|
| OODBMS |
Object-Oriented Database Management System |
| OOPL |
Object-Oriented Programming Language |
| OS |
Operating System |
| OSF |
Open Software Foundation |
| OSF-DCE |
OSF Distributed Computing Environment |
| OSF-DME |
OSF Distributed Management Environment |
| OSI |
Open System Interconnection |
| PBX |
Private Branch Exchange |
| PGP |
Pretty Good Privacy |
| PKI |
Public Key Infrastructure |
| QoS |
Quality of Service |
| QPSK |
Quadrature Phase Shift Keying |
| RDA |
Remote Database Access |
| RFID |
Radio Frequency Identification |
| RPC |
Remote Procedure Call |
| SCM |
Supply Chain Management |
| SET |
Secure Electronic Transaction a security standard |
| SNMP |
Simple Network Management Protocol - TCP/IP Network management
Protocol |
| SOAP |
Simple Object Access Protocol part of Web Services |
| SONET |
Synchronous Optical Network |
| SQL |
Structured Query Language |
| SSL |
Secure Socket Layer |
| TCP |
Transmission Control Protocol |
| TCP/IP |
Transmission Control Protocol/Internet Protocol |
| UDDI |
Universal Description, Discovery and Integration - a registry
for Web Services |
| UDP |
User Datagram Protocol - a protocol that runs on IP
|
| UMTS |
Universal Mobile Telecommunication System (Mainly 3G Cellular
Technology) |
| UWB |
Ultra Wideband |
| VAN |
Value-added Network |
| VPN |
Virtual Private Network |
| VXML |
Voice eXtensible Markup Language |
| WAN |
Wide Area Network |
| WAP |
Wireless Application Protocol |
| WLL |
Wireless Local Loop |
| WML |
Wireless Markup Language |
| WS |
Web Services |
| WSN |
Wireless Sensor Network |
Publishing content on the web is one of the oldest application of web. You
basically store your files (HTML/XML) on a web server so that the customers
can access this content through Web browsers. The growing number of Web
sites that publish content (known as "resources") to be accessed
transparently by Web users is the main strength of WWW. Examples of the Web
sites at present are corporate Web sites, university Web sites,
publishing/advertising Web sites, travel agency Web sites, and small
business Web sites. Web sites can be large (e.g., large corporations may
dedicate several machines as Web sites) or small (smaller companies may rent
or lease portions of a Web site).
Although conceptually a Web site is a catalog of information for each
content provider over the Web, in reality, a Web site consists of three
types of components: :
Setting up a Web site involves a large number of issues such as the
following:
Web publishing represents the C2B - information services business
pattern.
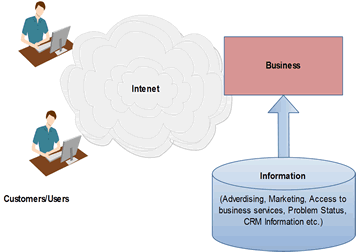
In this pattern, the enterprises are mainly information providers. No
purchasing takes place (that is a different business pattern).
This is one of the oldest model of Web and is largely used for
advertisements and information dissemination through Web sites. Users, who
can be either internal or external to the enterprise, interact with
enterprise transactions and data. In some cases, there may be a need to
access back-end applications and data. This pattern is relevant to those
enterprises dealing with goods and services not normally listed in and sold
from a catalog. It encompasses all user-to-business interactions not covered
by the User-to-Online Purchase pattern. Many (but not all) of the functions
supported by the User to Business pattern relate to Customer Relationship
Management (CRM) systems.
The application provider, in the following discussion, may be an outsourced development
house or an internal software development group.
For Interoperability: A common approach used in interoperability is an ontology
mapping table (OMT). Simply stated, ontology represents a vocabulary. An OMT translates
the terms in one system to the other and thus provides the bridge between disparate
systems (see a simple example below).
Many organizations are pushing the use of the Semantic Web (with XML) for interoperability
with focus on eGovernment, eHealth or eBusiness. Examples are:

 Business
Pattern
Business
Pattern