|
Service Synopsis:
Distance Learning and eLearning
Service
1. Name of the
eService
Distance Learning
(General)
2. Government Agency
Education
(E-Learning)
3. Overview (one paragraph
with a conceptual diagram view)
Simply
stated, e-learning comprises all forms of electronically supported
education (i.e., e-education). This term is most commonly used for distance learning over the Internet where the remotely located students and
instructors are interconnected through the Internet. Developments in Internet
and multimedia technologies are the basic enablers of e-learning. In modern
settings, e-learning typically includes Web/computer-based learning, virtual
classrooms and digital collaboration. Content is delivered via the Public
Internet, and intranet/extranet via media such as text, image, animation,
streaming video and audio. e-Learning is being used heavily in K-20
and professional education. In some cases, e-learning is 100% online, with a
mixture of synchronous and asynchronous methods (explained below).
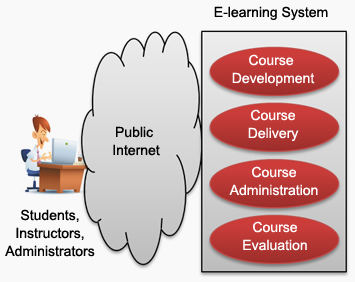
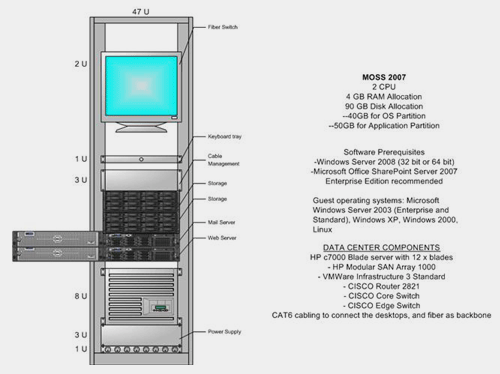
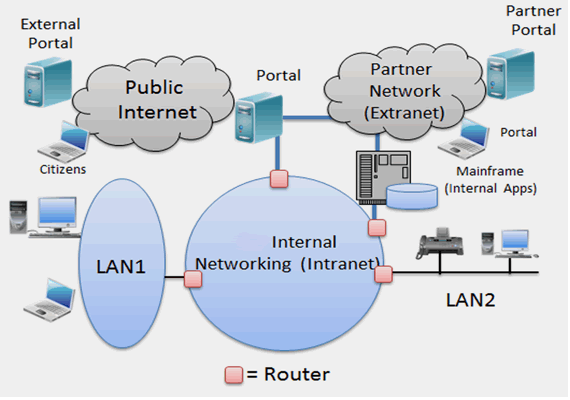
e-Learning systems, as shown
in the diagram, consist of the following key components:
Course
development capabilities in electronic format
Course delivery
mechanisms, typically over the Internet
Course
management and administration facilities over the Internet
Course
evaluation (e.g., exams and quizzes) over the Internet
The e-learning content is
delivered by using the asynchronous (self-paced), synchronous (instructor-led)
or mixture (e.g., virtual classroom) communications:
Asynchronous
communications allow participants to engage in the exchange of information
without the dependency of other participants involvement at the same time. These
activities use technologies such as email, blogs, wikis, and discussion boards.
Asynchronous e-learning gives students the ability to work at their own pace,
thus reducing stress and scheduling problems.
Synchronous
communications involve the
exchange of information between several participants during the same period of
time. A telephone call (through Skype, for example) or face to face discussion
is an example of synchronous communication. Synchronous e-learning is typically
instructor led and requires all participants to join in at once, as with a
telephone conference call or an online chat session.
Mixtures
of communication
technologies are used in many e-learning environments. A good example is a
virtual classroom environment. In virtual classrooms, participants use icons
called emoticons (e.g., smiley faces) to communicate feelings and responses to
questions or statements. Virtual classrooms commonly include text notes,
microphone rights, and breakout sessions that allow the participants to work
collaboratively in a small group setting to accomplish a task or to have
private conversations with the instructors. Participants can also use a
white board for discussions. Some virtual classrooms also allow sharing of
desktops, with proper permissions. In short, virtual classrooms attempt to
simulate as close to a real classroom environment as possible.
From Distance Learning to e-Learning
2.0
Distance
learning implies education for people who are not physically close to the
instructors. The term e-learning in the modern settings implies distance
learning by using the Internet and the Web. e-Learning 2.0 goes a step beyond by
relying on Web 2.0. Conventional e-learning systems are based on
asynchronous model where instructional packets are delivered to students over
the Internet, assignments are sent to the instructor through email, and sent
back with evaluations. e-Learning 2.0 places increased emphasis on social
learning by using the Web 2.0 software such as blogs, wikis, podcasts and
virtual worlds (e.g., Second Life). e-Learning 2.0 is much more
synchronous than the conventional e-learning it relies on conversations about
content. e-Learning 2.0 also uses virtual classrooms (online and discussion
forums) as an online learning platform. Terms such as Mobile Assisted
Language Learning (MALL) are used to describe language learning through handheld
devices.
| Business Strategy Assessment | | Goal of subject ICT service | Provide New Service to Existing Customers | | Source of Funding | Current Business Budget | | Alignment of Service with Business Strategy | Directly (primary value) | | Governance | Accountability. Equity. Participation. Rule of Law. Transparency. | | Parameters | Present Mode of Operation | Future Mode of Operation | | Service Availability | Not available at all | Available to 20% of the population | | Service Quality | Non Existing, intolerable | Mostly bad, occasionally good | | Provider Service Management | Non Existing | Initial, Ad hoc | | Business Strategy for the Service | Non Existing | Vision Mission defined | | Legal, Technical and Human Infrastructure | Non Existing | Policies have been defined | | Overall Management, Technical and Human Infrastructure of Small to Medium Businesses | Non Existing | Policies have been defined | | Ability to Detect problems | - | - | | Ability to Adjust quickly | - | - | | Ability to Learn for future improvements | - | - |
|